Open-Source Toolchains in Functional Safety: Can You Use Them?
Why open-source toolchains raise questions?
Open-source toolchains in functional safety raise important questions about qualification, trust, and when certified tools are really necessary. Many engineers still assume that using only certified tools is the safest or even the only compliant option. In reality, standards usually ask for a justified qualification and confidence-in-use argument, not for a specific vendor label on the tool. The key challenge is to decide when open-source toolchains in functional safety are acceptable, and how to demonstrate enough confidence in them to satisfy standards and assessors.
With the right qualification approach, even open-source or custom-developed toolchains can support functional safety projects. The essential point is that the toolchain must be understood, monitored, and supported by suitable checks and evidence.
Discussion at the ELISA workshop
This topic took center stage at the recent ELISA Project Workshop in Munich. In a featured talk, Christopher Zimmer explored how open-source ecosystems and safety-critical development can work together, using the X-as-code concept as a structured way to manage safety and compliance lifecycles.
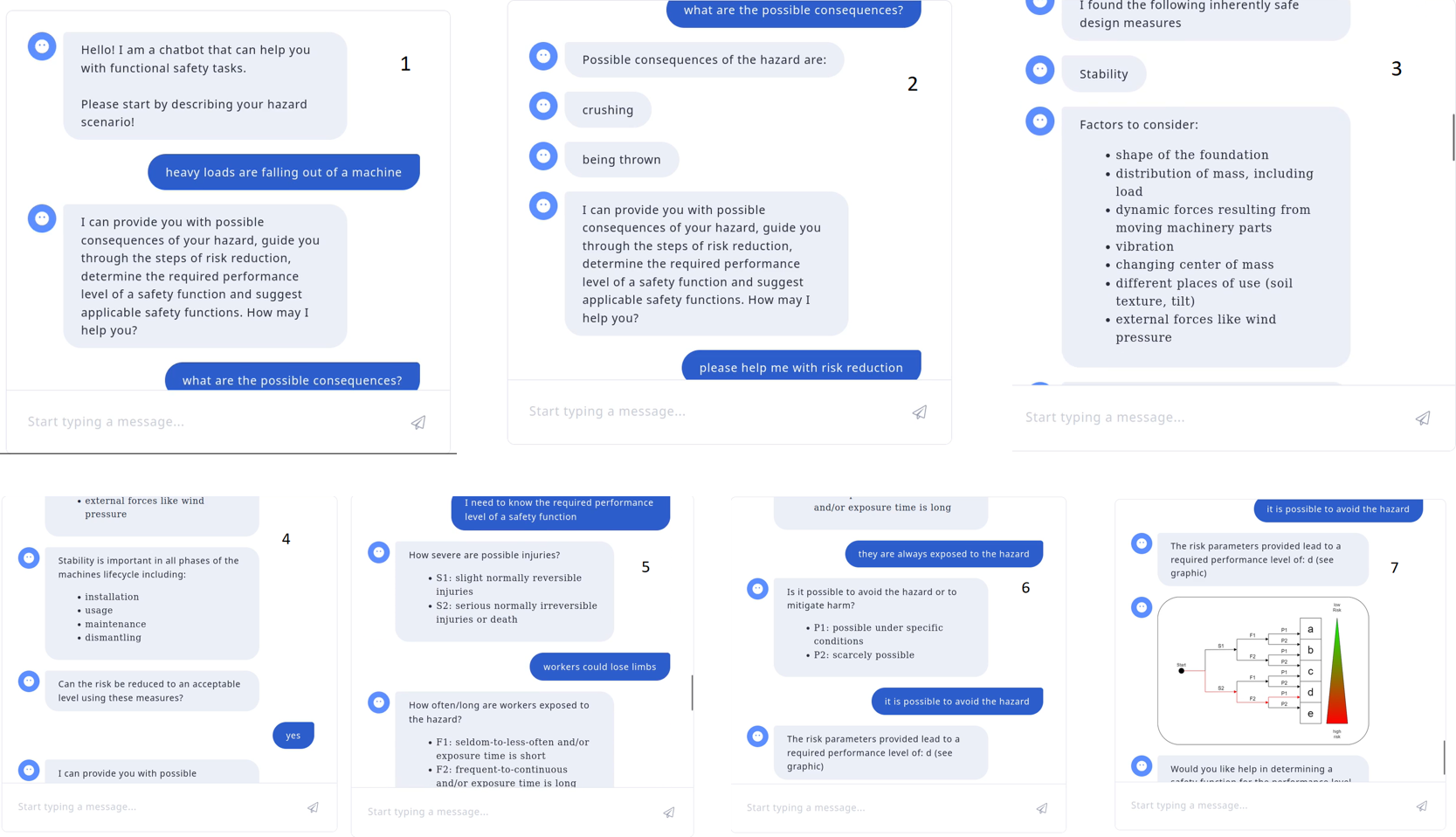
Using tools such as Sphinx and Sphinx-needs, he showed how documentation, traceability, and qualification activities can be automated and integrated into the engineering workflow, so that open-source toolchains in functional safety projects remain both agile and auditable.
From “certified only” to “qualified and justified”
A key takeaway is that the decision is not “open source versus certified” but “unqualified versus justified and qualified”. Teams can integrate open-source components into their safety toolchains if they define tool confidence levels, identify possible failure modes, and put mitigations and checks in place. This leads to a transparent toolchain where both commercial and open-source tools are selected and combined based on risk, evidence, and lifecycle needs rather than marketing labels.
As this ecosystem evolves, X-as-code becomes a powerful way to encode processes, roles, and safety artefacts directly in version-controlled repositories. Treating safety plans, requirements, and traces as code allows continuous integration pipelines to check completeness and consistency whenever something changes. Combined with open-source toolchains in functional safety, this approach enables repeatable, inspectable, and scalable safety and cybersecurity lifecycles.
What comes next?
In the new year, Christopher and the innotec team will offer webinars on the X-as-code approach for both functional safety and cybersecurity lifecycles. These sessions will include live demonstrations of Sphinx, Sphinx-needs, and related tooling in realistic project scenarios.
Participants will see when open-source toolchains in functional safety are appropriate, how to argue tool qualification, and how to implement these concepts in day-to-day engineering practice.
Stay tuned for more updates from innotec GmbH – TÜV Austria Group, including registration links and dates for the X-as-code webinars.