Advancing Industrial Drone Cybersecurity and Compliance
Once seen as toys for hobbyists, drones have quietly graduated to full-time industrial jobs: scanning pallets, ferrying parts, and feeding factory data systems. However, in the year 2025 for example, Germany logged a surge in unauthorized drone flights, including 35 near Frankfurt alone, sparking concern about surveillance and cyber risk to critical sites. Officials are now pushing for stronger defensive powers against drones approaching sensitive facilities. It’s a timely reminder that the air above our factories is becoming part of the cybersecurity landscape.
New Mobility, New Attack Surfaces
Every connected drone is a flying endpoint. It runs firmware that must be updated, exchanges telemetry and video over Wi-Fi or 5G, authenticates with backend APIs, and often integrates with Manufacturing Execution Systems or warehouse control software. Each of these links can be probed or exploited:
- Wireless compromise: interception, spoofing, or jamming can disrupt fleets or hijack control.
- Malicious firmware: supply-chain tampering or unverified updates can implant backdoors.
- Backend infiltration: weak APIs or identity management may expose factory networks.
- Data leakage: camera and sensor streams can reveal sensitive layouts, production data, or IP.
In safety-critical OT spaces, such weaknesses don’t just threaten confidentiality — they can stop lines, damage goods, or endanger people.
Regulation Raises the Stakes
Europe has tightened its stance on connected product security. The Radio Equipment Directive (RED) requires radio-enabled devices, including UAVs, to prove resilience against cyberattack and protect personal data and economic interests. The Cyber Resilience Act (CRA) expands this idea, mandating security-by-design and ongoing vulnerability management. Meanwhile, IEC 62443 remains a global anchor for industrial control system security.

These frameworks demand documented risk assessments that link realistic operating scenarios to credible cyber threats and show that mitigations are in place. For drones operating deep inside production zones, fulfilling these requirements is non-trivial.
The Industry Challenge
Risk assessments today are still largely manual, expert-driven, and time-consuming. They require deep knowledge of drone architectures, OT environments, and regulatory texts. Few companies can spare enough specialists to analyze every flight profile, communication channel, and update path.
It’s natural to ask: can artificial intelligence, especially large language models (LLMs) help automate parts of this work? AI can already summarize vulnerabilities and generate documentation. Could it also suggest likely threats for a given industrial drone scenario?
The obstacle is trust. Until recently, there was no way to measure whether LLMs truly understand UAV–OT cybersecurity in a regulatory context. Without measurement, adoption is risky, output might appear polished but omit key threats, creating a false sense of security.
Bringing Measurement and AI Together
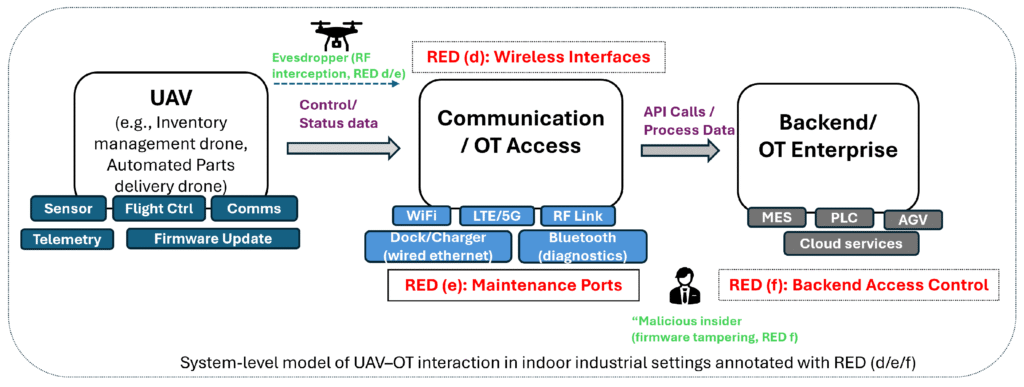
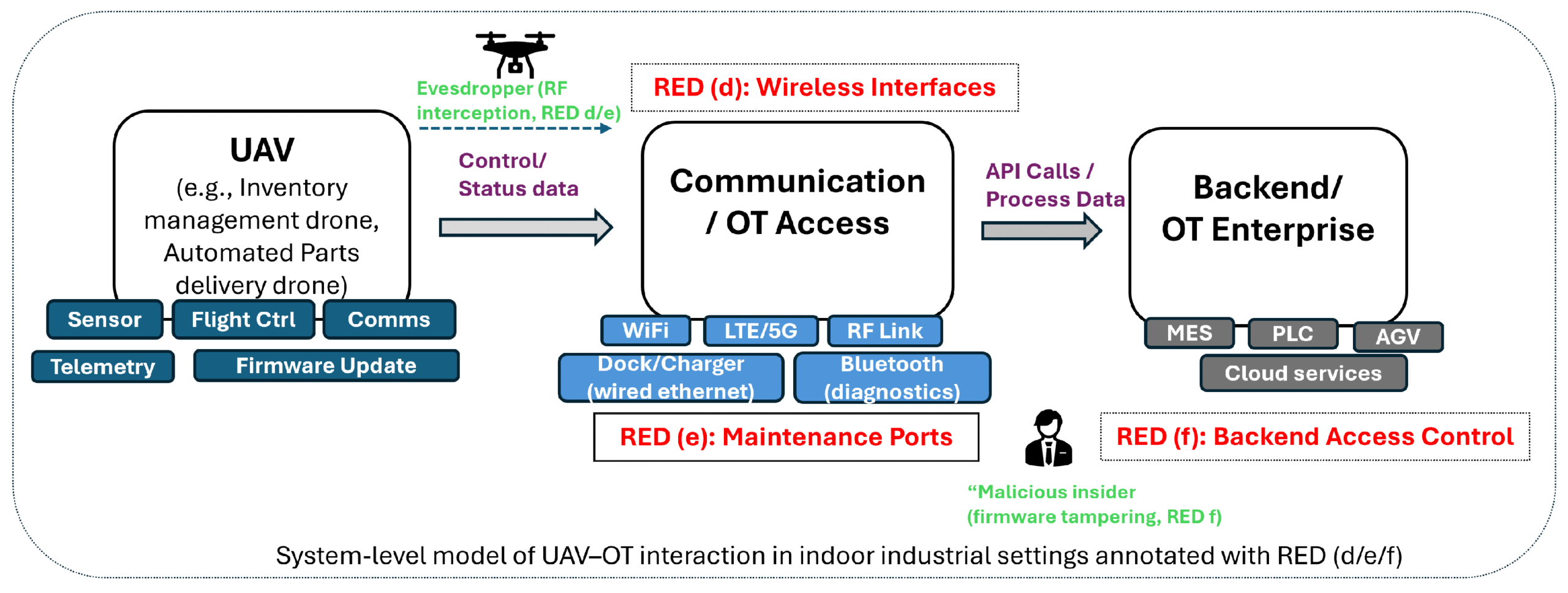
To make AI use in security engineering trustworthy, our senior expert Dr. Padma Iyenghar at innotec GmbH – TÜV Austria Group developed UAVThreatBench: the first open, RED-aligned benchmark for evaluating how well large language models (LLMs) identify cyber threats in industrial UAV/OT deployments. The dataset provides:
- Evaluation capability: a structured ground truth enabling reproducible testing of LLM outputs for regulatory completeness.
- Realistic industrial scenarios: 924 drone operations representing warehouse and factory use (fleet coordination, wireless telemetry, firmware updates).
- Expert-curated threats: 4,620 mapped to RED Articles (d/e/f) and structured using IEC 62443 risk concepts.
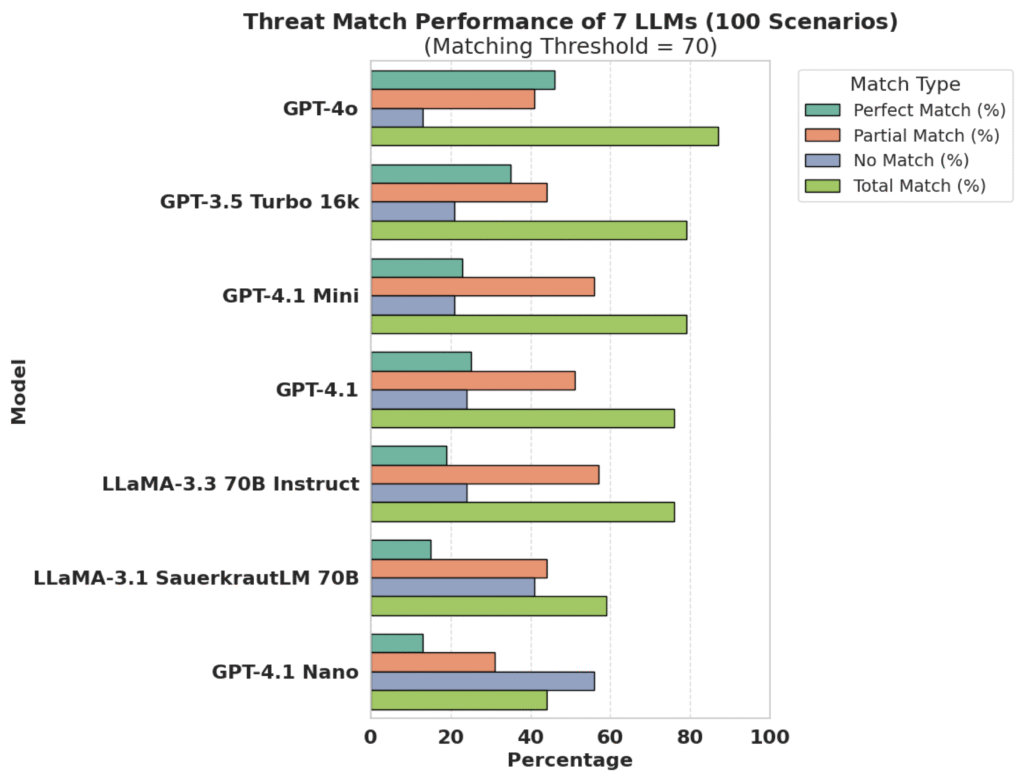
A recent evaluation carried out using the UAVThreatBench dataset on both state-of-the-art proprietary LLMs (such as GPT-4o and GPT-3.5 Turbo) and leading open-source models (e.g., LLaMA-3 variants) showed that while advanced models detect many access and confidentiality issues, they consistently miss availability and backend manipulation risks vital for RED and CRA compliance; open models performed even weaker. Proprietary, instruction-tuned models like GPT-4o achieved up to 87 % total threat match but still failed on availability and backend manipulation risks critical for RED and CRA compliance; open-weight LLaMA variants trailed further, with only 15–19 % perfect matches. The study shows AI can assist threat enumeration but remains incomplete for safety-critical, regulation-driven assessments.
The complete dataset and evaluation results on LLMs are available as open-source dataset in a GitHub repository.
Full Evaluation Details
UAVThreatBench: A UAV Cybersecurity Risk Assessment Dataset and Empirical Benchmarking of LLMs for Threat Identification
Complete methodology and results are published open access in MDPI Drones 9(9), 657 (2025):
Why it matters?
- For manufacturers and integrators, the published UAVThreatBench evaluation provides an objective way to validate AI models before using them in RED, CRA, or IEC 62443 compliance workflows.
- For standards bodies and regulators, the openly documented methods and results show a transparent, reproducible approach to measure AI reliability in safety-critical industrial domains.
- For innotec customers, the openly available study demonstrates how combining deep standards expertise with rigorous benchmarking makes security-by-design measurable and auditable.
innotec is actively engaged in cybersecurity risk assessment and the design and implementation of secure process workflows across complex OT environments, helping leading industrial clients meet RED, CRA, and IEC 62443 requirements while embedding practical, measurable security-by-design into their development and certification processes. If your organization wants to strengthen product security, integrate trustworthy AI support, or prepare for upcoming regulatory demands, get in touch with our experts to explore how we can make your cybersecurity and compliance journey more effective and auditable.