Security by Design in OT: Why Structured Processes Matter
In Operational Technology (OT), cybersecurity is not just about firewalls or intrusion detection, it’s about ensuring that critical systems such as safety components, PLCs, HMIs, and industrial networks remain safe and reliable, even under attack. These systems often run on legacy infrastructure, have long life cycles, and are tightly coupled with safety-critical operations. This necessitates a proactive approach, OT security by design, making it a continuous engineering concern, not an isolated task, especially given the legacy infrastructure and long life cycles of these systems.
What about Standards?
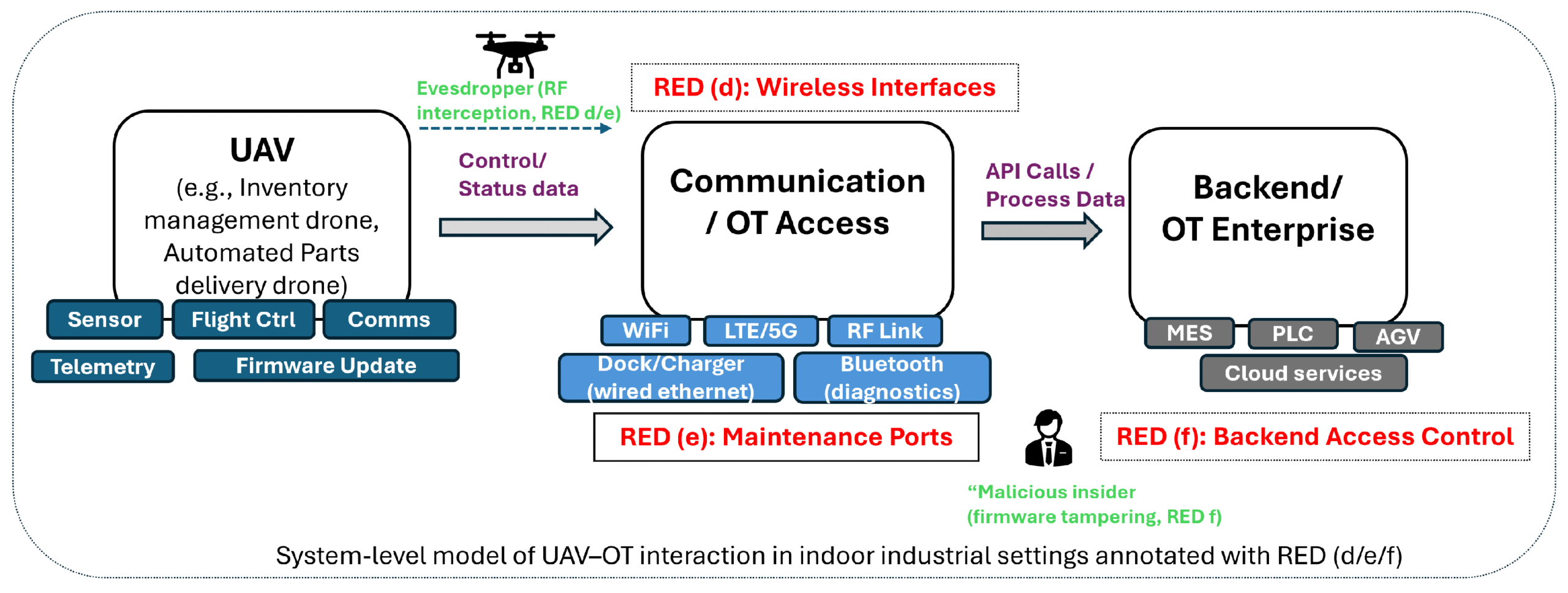
There is growing regulatory pressure to secure OT environments, yet the standardization landscape remains fragmented. The EN 18031 series, under the Radio Equipment Directive (RED), is currently the only harmonized cybersecurity standard—and it applies only to wireless-connected devices.
Other frameworks such as IEC 62443 provide important guidance but are not harmonized. As a result, companies must currently demonstrate on their own how their practices meet regulatory expectations—typically through technical documentation, risk assessments, internal audits and several discussions about “which standards should we use”.
In life and in upcoming regulation, you never know what’s coming, but you must be prepared.
Instead of focusing on whether a specific standard is harmonized or not, a more practical and useful question is: How do you ensure your OT systems are secure by design?
Security by Design Starts with Systematic Processes
Security in OT cannot be managed through ad hoc decisions or occasional compliance checks. It must be built into how systems are developed, integrated, and operated—from initial design to ongoing maintenance.
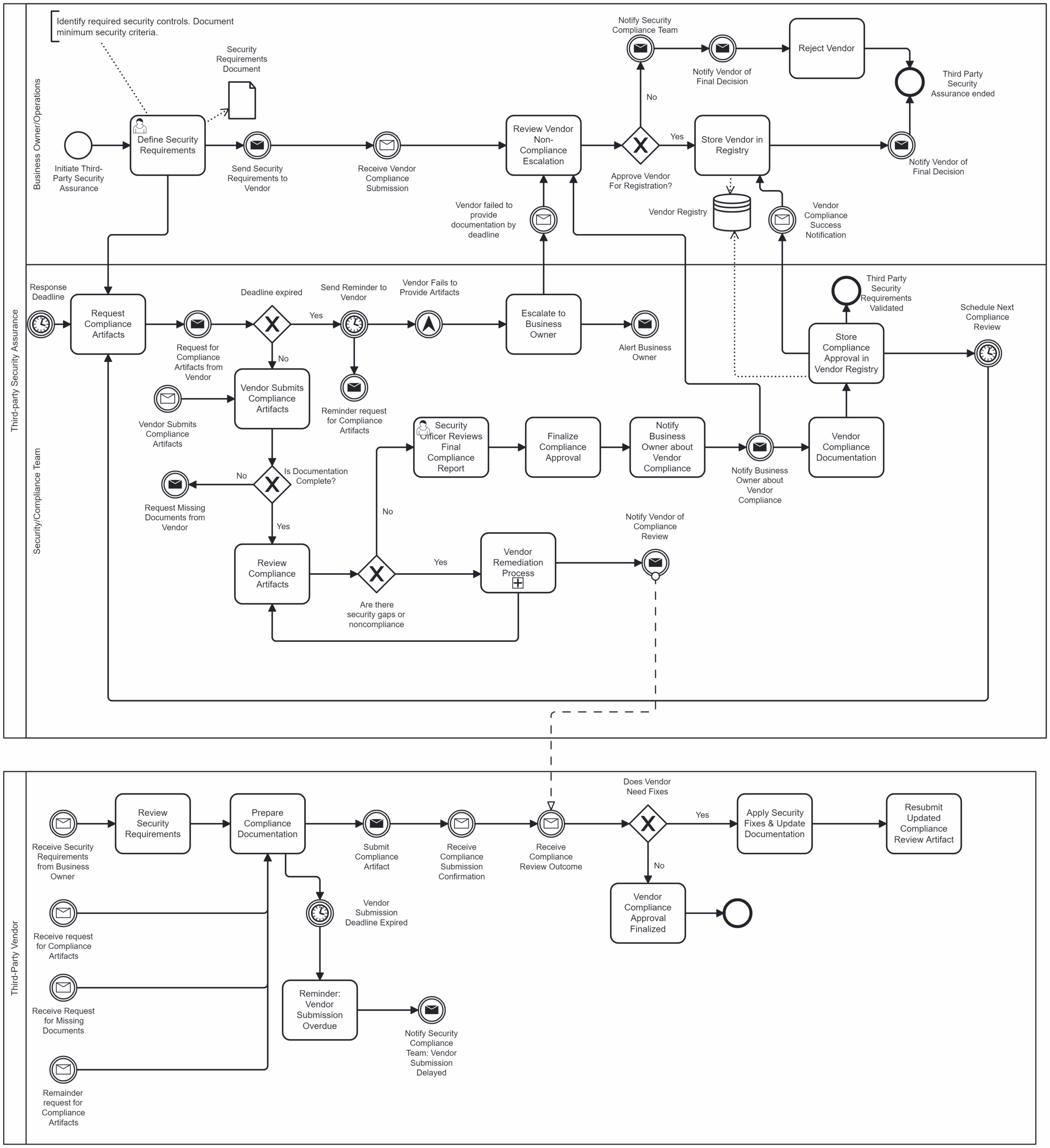
Implementing OT cybersecurity by design means defining structured processes that ensure cybersecurity is addressed early, consistently, and with traceability. These processes should guide critical activities such as:
- Threat and risk analysis
- Secure architecture reviews
- Implementation of technical controls
- Verification and compliance checks
- Ongoing vulnerability and patch management
Without such processes, even well-intentioned teams will struggle to meet regulatory or operational expectations.
How to Get Started
First: you don’t need to wait for harmonized standards to begin. They will not re-invent the wheel; instead, a robust OT cybersecurity by design approach can be implemented today by following a few key steps:
- Analyze your current process landscape
Identify which cybersecurity activities (even if not documented yet) are already embedded into your OT workflows and where the gaps are. - Align with good practices like IEC 62443
Use existing frameworks to guide the definition of roles, responsibilities, and lifecycle phases for cybersecurity. - Formalize your processes systematically
Represent your workflows using clear documentation or standardized modeling approaches such as BPMN, and realize them through practical tools—whether spreadsheets, wikis, or platforms like Jira.
Our Experience
At innotec, we are already supporting small, medium and large industrial clients in defining and operationalizing OT cybersecurity processes. By translating good practices into clear, actionable workflows, we’ve seen teams improve traceability, reduce audit issues, and effectively preparing for the upcoming Cyber Resilience Act and Machinery Regulation.
You don’t need to wait for harmonized standards to take action. The foundation for secure OT systems starts with structured processes aligned with real-world operations.
Contact us to learn more about how we can support your cybersecurity readiness journey.