Current State-of-the-Art in the Design of Robust and Secure Embedded Software
Functional safety and cybersecurity for embedded software systems have become essential concerns across automotive, medical, and industrial domains.These systems must operate safely and securely because failures can lead to severe outcomes, from operational downtime to serious human injury. In this article, we discuss how to design robust and secure embedded software. Robustness and security are distinct but related aspects critical to ensuring system reliability and user trust, i.e., dependability of embedded systems.
What are Robust and Secure Embedded Systems?
Embedded systems are specialized computing systems, for example within larger mechanical or electrical systems. They operate under real-time constraints and have limited resources like memory and processing power.
Robust systems handle internal faults effectively and are a key aspect of functional safety. Functional safety ensures systems remain safe, despite software malfunctions or faults. Secure systems defend against external threats such as cyber-attacks, unauthorized access, and data manipulation.
Robustness: Fault-driven Risks
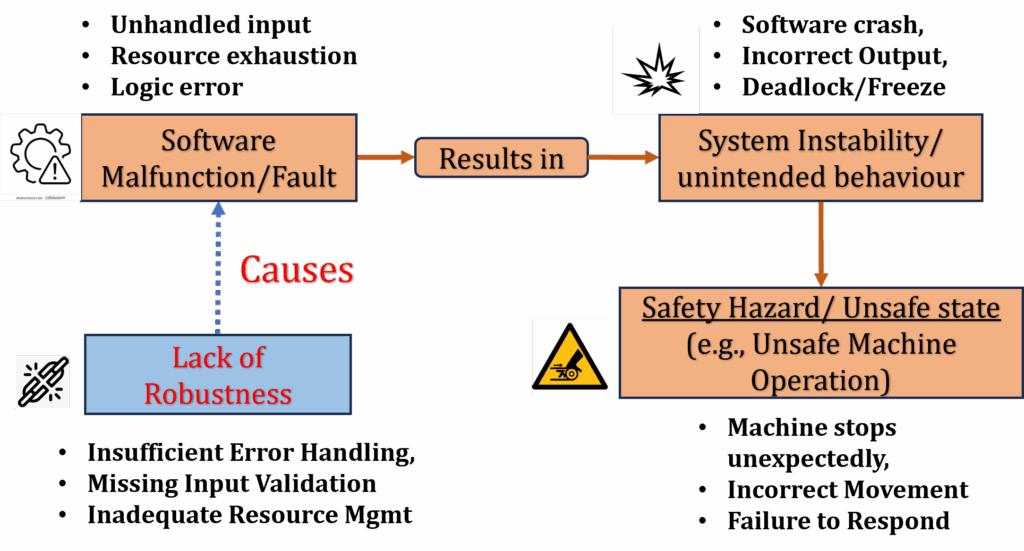
Robust software detects and manages faults internally to keep systems safe. Examples of common software faults include, unhandled inputs, resource exhaustion and logic errors. These faults cause issues such as software crashes, incorrect outputs and system freezes. Without proper robustness, embedded software may result in dangerous situations, such as a machine stopping unexpectedly or behaving unsafely as illustrated in Figure 1 below.
Security: Threat-driven Risks
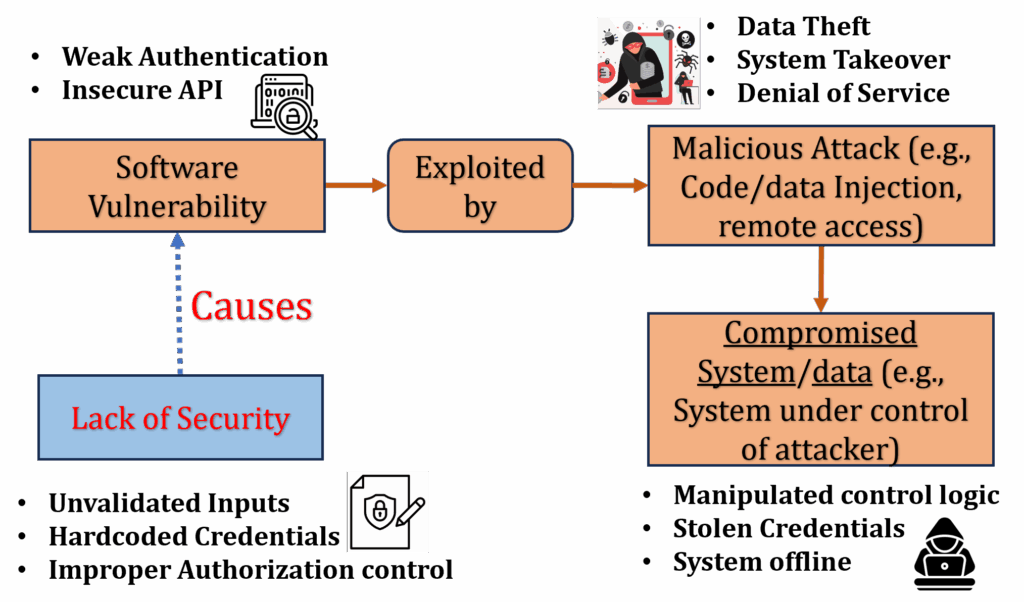
Secure software protects against external threats. Typical security vulnerabilities include weak authentication, insecure APIs and improper authorization. These vulnerabilities can lead to data theft, system takeover and denial of service (DoS). Without robust security, systems may become compromised, allowing attackers to control system operation or steal sensitive data as explained in the Figure 2.
Understanding IT and OT environments
Before we discuss further safety and security mechanisms and best practices, it is important to understand the differences between Information Technology (IT) and Operational Technology (OT). They represent two distinct areas within an organization, each serving specific functions, as shown in Figure 3.
IT handles business-related data through systems like SQL databases, cloud computing services, customer relationship management (CRM), and enterprise resource planning (ERP) software. It also uses protocols like Remote Desktop Protocol (RDP) and HTTP for general internet access and data exchange.
On the other hand, OT manages physical equipment and industrial processes, including machinery, assembly lines, remote terminal units (RTUs), and human-machine interfaces (HMIs). It involves systems such as Supervisory Control and Data Acquisition (SCADA), programmable logic controllers (PLCs), and industrial communication protocols like MODBUS.
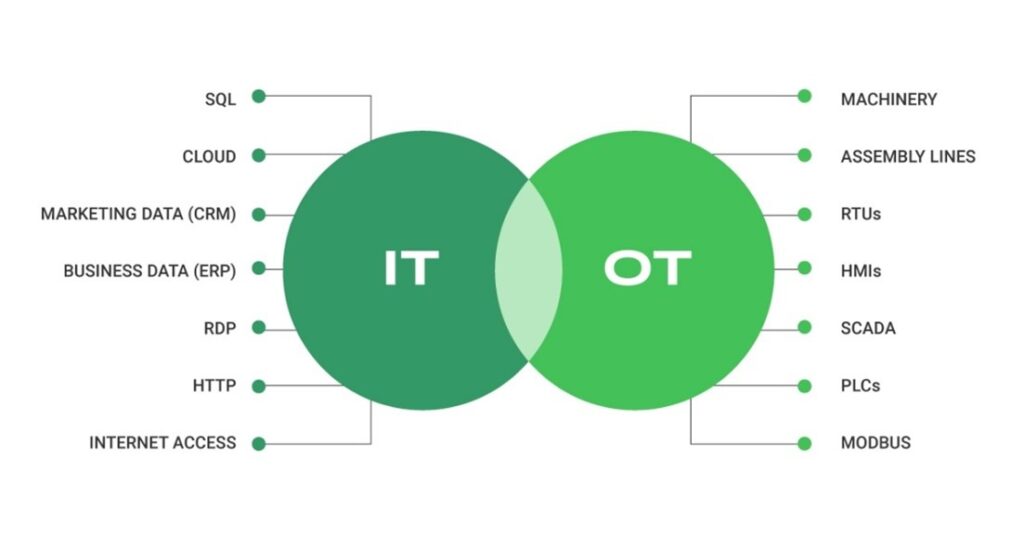
The intersection in the figure shows increasing integration between IT and OT systems, highlighting how closely these two domains now collaborate. This integration brings benefits such as improved operational efficiency, but it also creates new cybersecurity risks. Therefore, clearly understanding both the distinctions and connections between IT and OT is essential for ensuring overall operational safety and robust cybersecurity. From now on, we will concentrate on cybersecurity aspects in OT environment as the scope in this blog article (and not IT cybersecurity).
State-of-the-art: Standards and Best Practices
Standards are critical for developing safe and secure embedded systems. Key standards include IEC 61508 (general functional safety), ISO 26262 (automotive functional safety), and IEC 62443 (Operational Technology cybersecurity). These standards provide guidelines to ensure functional safety and cybersecurity for embedded software systems are addressed effectively throughout the entire product lifecycle.
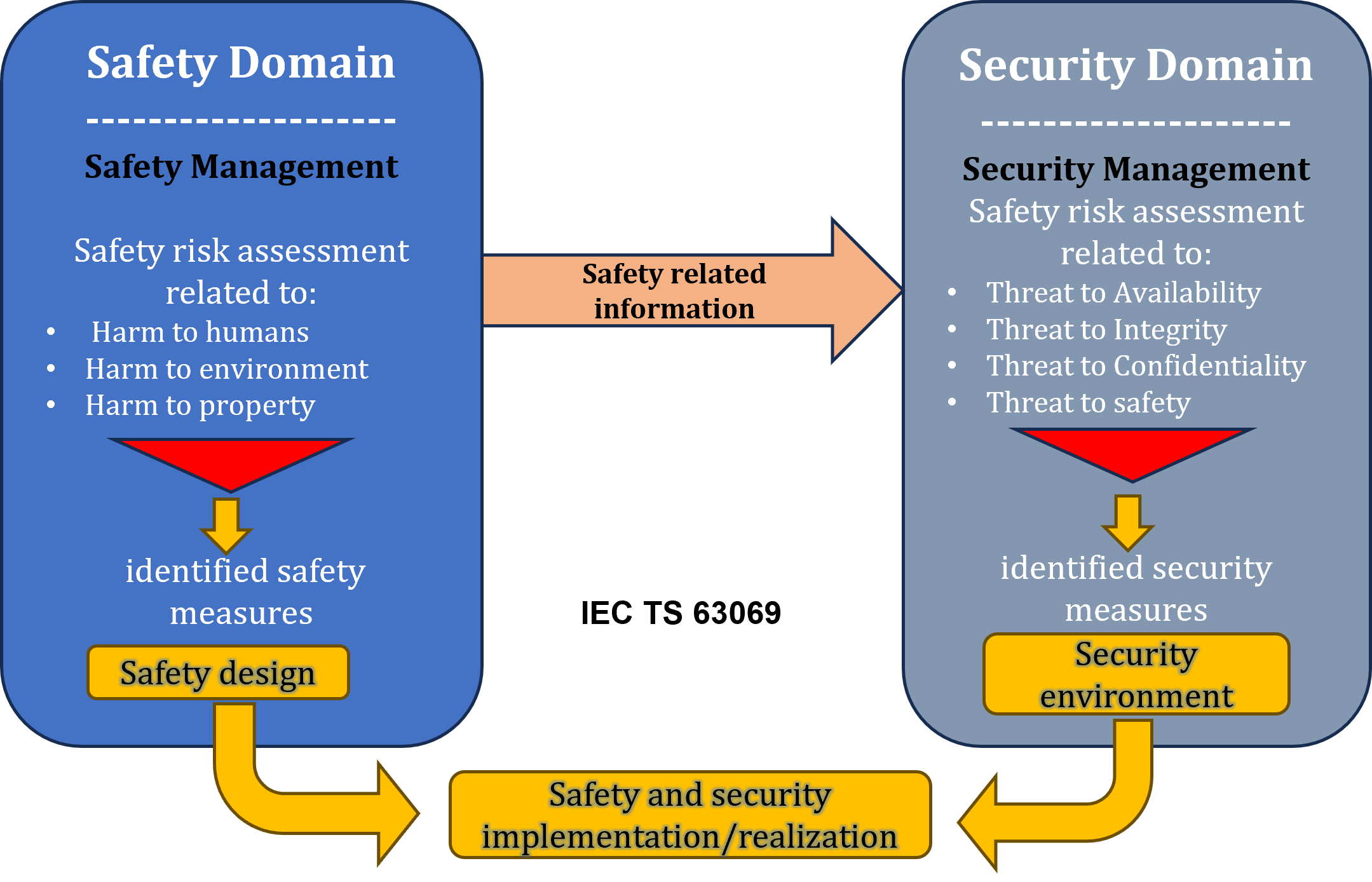
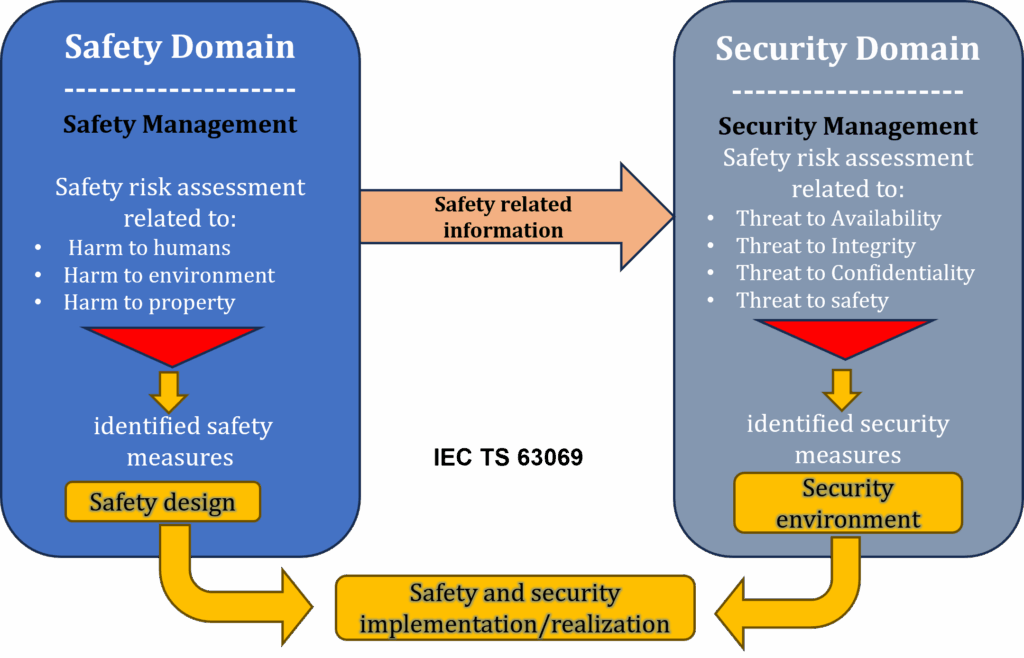
State of the art refers to the most advanced, proven, and widely accepted practices in industry and academia. These standards help embed those practices into structured development and certification processes. Figure 4 below illustrates how safety and security domains—though distinct—interact closely. Safety focuses on risks such as harm to humans or the environment. Security addresses risks related to availability, integrity, and confidentiality. Together, they guide the implementation of safety designs and secure environments in embedded systems.
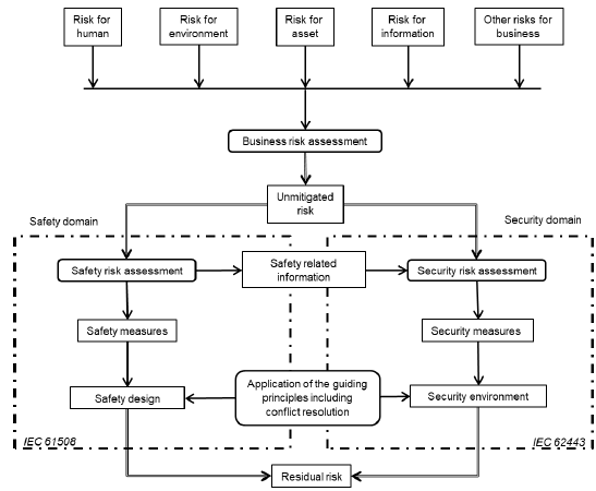
Furthermore, Figure 5 provides an integrated risk management view based on IEC 61508 and IEC 62443. It shows how both safety and security risk assessments contribute to a unified business risk strategy. This integration enables harmonized measures and helps resolve conflicts between safety and security requirements. Figure 4 and Figure 5 reinforce the importance of applying both domains cohesively to manage residual risks effectively and to achieve compliance in safety-critical environments.
Safety Mechanisms
Safety mechanisms for embedded systems involve the functional safety lifecycle as detailed comprehensively, for example, in IEC 61508-3. This lifecycle includes hazard analysis, defining software safety requirements, and emphasizes traceability with a controlled development process. Key practices include:
- Safety-oriented architecture, such as modular design, watchdog tasks, fault containment, and fail-safe transitions.
- Defensive programming and error detection and correction.
- Redundant code paths (e.g., N-version programming).
- Runtime checks for value range and plausibility.
- Memory protection and voting logic.
- Formal development techniques, including adherence to coding standards like MISRA .
- Rigorous verification methods, such as fault injection, coverage tests, and timing analysis for compliance.
These structured approaches ensure systems tolerate faults effectively during operation and maintain safe functionality.
Security Mechanisms
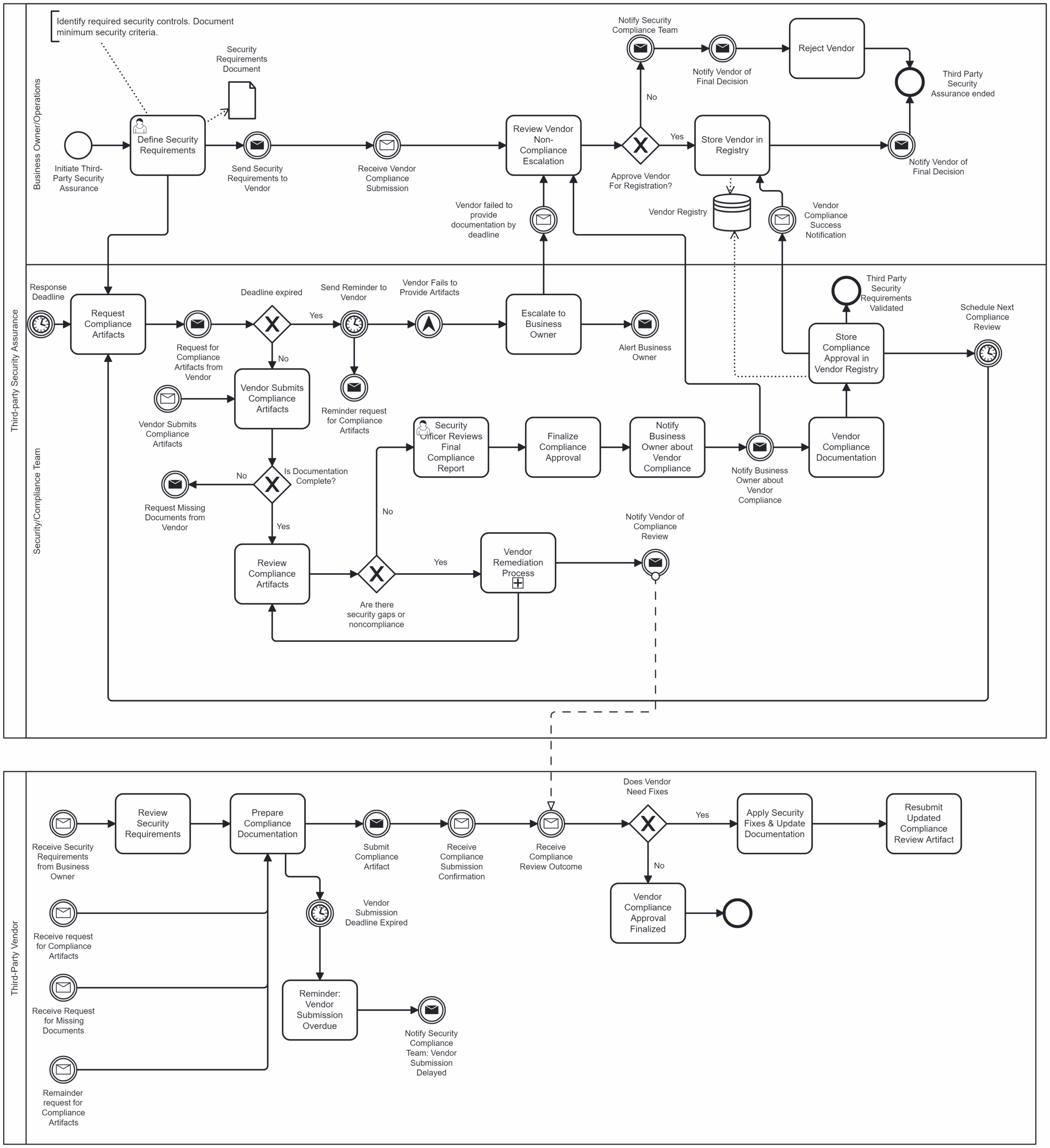
The Figure 6 shows how security weaknesses are often introduced early—during design and development—but discovered much later, after deployment or in maintenance. Fixing issues at later stages is much more expensive. The red bar shows this rising cost. That’s why it is important to include (“bake in”) security right from the start of the product lifecycle. Early action reduces both risk and cost.
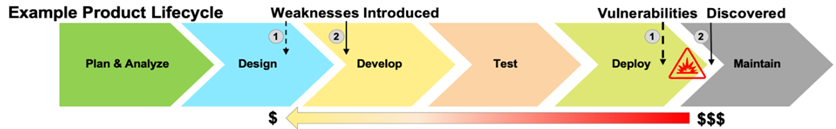
Security mechanisms for embedded systems follow a structured Secure Development Lifecycle (SDLC) as comprehensively outlined in IEC 62443-4-1. This lifecycle involves continuous governance, training, and compliance monitoring, alongside rigorous technical practices throughout all development phases. Key aspects include:
- Governance: Establishing security policies, developer training, and adherence to regulatory compliance.
- Design Phase: Performing threat modelling (e.g. MITRE EMB3D framework), specifying security requirements, and designing secure system architectures.
- Implementation: Adhering to secure coding standards such as SEI CERT guidelines and mitigating common coding weaknesses (Common Weakness Enumeration-CWE).
- Verification and Testing: Conducting thorough security testing, including architecture reviews and vulnerability assessments.
- Deployment and Operations: Ensuring incident response readiness, proactive patch management, and continuous tracking of Common Vulnerabilities and Exposures (CVE).
- Security Architecture: Incorporating secure boot procedures, firmware signing, encryption techniques, and secure-by-default configurations.
Security is managed continuously, from initial design through deployment and maintenance, with regular updates and patches to address newly discovered vulnerabilities. This comprehensive approach ensures embedded systems remain resilient against evolving cybersecurity threats throughout their operational lifespan.
Real-World Example: Functional Safety and Cybersecurity in Embedded Systems
Autonomous vehicles require the tight integration of functional safety (FuSa) and cybersecurity (CS) to ensure both safe behavior and protection against external threats. Functional safety ensures the vehicle responds correctly to faults, such as sensor failures or control errors, by transitioning to a safe state. Cybersecurity protects the vehicle from attacks that could compromise its systems, like unauthorized access or data manipulation.
One real-world example is Traffic Sign Recognition (TSR), which detects and interprets road signs to support driver decisions. Even without AI, such functions must be both robust—handling sensor faults or signal occlusion—and secure—resisting spoofed signs or manipulated input data. This integration of FuSa and CS is supported by domain-specific standards, as listed below, that guide the development of safe and secure vehicle systems. This shows how FuSa and CS work together to maintain reliable operation under both internal failures and external attacks.
- Functional Safety: ISO 26262 to ensure for example, robust sensor fusion, diverse architectures, and rigorous robust testing.
- Cybersecurity: ISO/SAE 21434 to cover for example secure Over-The-Air (OTA) updates, secure boot processes, and intrusion detection systems (IDS).
What about AI/ML in automotive software?
Recent research conducted by innotec in collaboration with Cariad SE (Volkswagen group) focuses on the challenges of verifying and validating AI-driven software for automotive safety. This research provides a systematic approach to integrating AI/ML into functional safety frameworks. Key elements include developing new testing methods specifically tailored for AI models, ensuring robustness against adversarial attacks, and verifying model interpretability and explainability. These contributions to the state-of-the-art are vital for managing the complexities of AI/ML integration in critical systems, such as autonomous vehicles. This research serves as a practical example of how emerging challenges with AI-driven technologies can be systematically addressed to meet rigorous automotive safety standards.
Future Developments
The Cyber Resilience Act (CRA), mandatory by mid-2027, will further strengthen security requirements. Manufacturers must adopt cybersecurity-by-design, comprehensive risk assessment, and proactive vulnerability management. Future trends include Zero Trust architecture (“Never trust, always verify”), Post-Quantum Cryptography (PQC) and safe and secure AI/ML.
Conclusion
Robustness and security form the core of trustworthy embedded systems. Compliance with standards (e.g., IEC 61508, ISO 26262, IEC 62443) is essential for CE marking and marketing within the EU. In conclusion, achieving functional safety and cybersecurity for embedded software systems is essential for regulatory compliance, system integrity, and user safety.
innotec is working actively in defining the standards IEC 61508, ISO 26262 and IEC TR 63069 and related new editions. Staying up-to-date is the key. Feel free to contact us in case of any questions.